Symmetric-key algorithm
A symmetric cryptosystem is a cryptosystem in which, unlike an asymmetric cryptosystem, both participants use the same key. In some symmetric methods (e.g. IDEA), the two keys are not identical, but can be easily calculated apart. This article is limited to the presentation of encryption methods. Sometimes Message Authentication Codes are also referred to as a symmetric cryptosystem.
Formally, a symmetric encryption scheme is a tuple 







Symmetric methods are divided into block cipher-based methods and stream ciphers. With stream ciphers, the plaintext is encrypted character by character to obtain the ciphertext, or decrypted to obtain the plaintext. A block cipher works with a fixed block size and encrypts or decrypts several characters in one step. In order to be able to encrypt texts of any length with it, operating modes are defined that determine how the block cipher is used.
The major disadvantage of symmetric methods is the use of one and the same key for encryption and decryption, i.e. in addition to the encrypted information, the key must also be transmitted. The problem with using symmetric methods is that the key must be transmitted over a secure channel, because the security of the method depends on the secrecy of the key. In the past, the key was typically delivered in person by a messenger. Since the 1970s, asymmetric key exchange protocols have been known in the form of Diffie-Hellman key exchange, which can also be used to transmit keys securely over a wiretapped channel. Another possibility is to use asymmetric encryption methods to encrypt the symmetric key itself and thus be able to transmit it in a protected manner even over an insecure channel. With this hybrid encryption, the advantages of symmetric encryption (for example, higher speed) can be exploited during communication, while the key is protected from access by an attacker by asymmetric encryption.
Symmetric methods have been around since ancient times. Until the 1970s, only symmetrical methods were known at all.
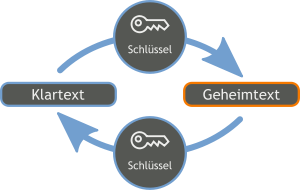
Encryption and decryption with the same key
Proceedings
- AES (Advanced Encryption Standard) or Rijndael: the U.S. encryption standard, successor to DES; block cipher developed by Joan Daemen and Vincent Rijmen.
- DES (Data Encryption Standard) or Lucifer: the US encryption standard until October 2000. Lucifer, the method, was developed by IBM in 1974. The version for private users is called Data Encryption Algorithm (DEA).
- Triple DES: a further development of the DES method; three times slower, but orders of magnitude more secure
- IDEA (International Data Encryption Algorithm): a block encryption method developed at ETH Zurich in 1990; software patented by Ascom Systec; used in PGP
- Blowfish: Block encryption method developed by Bruce Schneier in 1993, unpatented
- QUISCI (Quick Stream Cipher): very fast stream ciphering method developed by Stefan Müller in 2001, unpatented
- Twofish: Block encryption method, from the Counterpane team; used in Microsoft Windows, among others.
- CAST-128, CAST-256: Block encryption method by Carlisle M. Adams, unpatented
- RC2, RC4, RC5, RC6 ("Rivest Cipher"): several encryption methods by Ronald L. Rivest
- Serpent: Block encryption method by Ross Anderson, Eli Biham and Lars Knudsen, unpatented
- One-Time-Pad: unbreakable one-time key method by Gilbert Vernam and Joseph Mauborgne
Questions and Answers
Q: What is symmetric-key algorithms?
A: Symmetric-key algorithms is a method in cryptography where the keys for decryption and encryption are exactly the same shared secret.
Q: How can you generate the secret?
A: The secret can be generated randomly, or from a password, or through a secret key-exchange procedure like Diffie-Hellman.
Q: Why are symmetric-key algorithms important?
A: Symmetric-key algorithms are very important because they are faster on computers than public-key algorithms.
Q: What is public-key cryptography (asymmetric-key cryptography)?
A: In public-key cryptography (asymmetric-key cryptography) the key for encryption can be given to the public with no problem, and everyone can send you secret messages. The key for encryption is "open" because, in practice, it cannot be used to get the key for decryption.
Q: What are two kinds of symmetric cyphers?
A: Two kinds of symmetric cyphers include stream ciphers and block ciphers. Stream ciphers encrypt a message as a stream of bits one at a time while block ciphers take blocks of bits, encrypt them as a single unit, and sometimes use the answer later too.
Q: What size blocks do modern ciphers use?
A: Modern ciphers like the Advanced Encryption Standard use 128 bit blocks.
Q: What types of attacks have been used to exploit symmetry in history?
A:In history some cryptanalysis methods exploited symmetry so symmetric systems were less secure. Some attacks that have been used include known plaintext attacks, chosen plaintext attacks, differential cryptanalysis and linear cryptanalysis.
Search within the encyclopedia