Malware
![]()
The introduction is not sufficiently supported by evidence (e.g. itemised). Information without sufficient evidence may be removed soon. Please help Wikipedia by researching the information and adding good evidence.
See discussion page.
Malware [ˈmalwɛːɐ̯] - badware, evilware, junkware or malware [ˈmælˌwɛə] (a portmanteau of malicious and software) - refers to computer programs that have been developed to perform undesirable and possibly harmful functions from the victim's point of view. The term virus is often not clearly defined. Thus, the term virus protection is used to refer more generally to protection against malicious software of any kind.
Faulty software is to be distinguished from malware, although it can also cause damage itself or be exploited to attack computer systems due to security gaps or a lack of information security.
The malicious functions are usually disguised, or the software runs entirely unnoticed in the background (see below for typification). Malicious functions can be, for example, the manipulation or deletion of files or the technical compromise of a computer's security software and other security devices (such as firewalls and antivirus programs), but also the unsolicited collection of data for marketing purposes. It is also common for some malware to fail proper uninstallation by commonly used means, leaving at least software fragments on the system. These may continue to perform unwanted functions even after uninstallation.
The malware known so far can basically be divided into three different classes: Computer viruses, computer worms and Trojan horses.
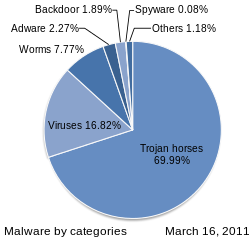
Malware statistics 2011. Trojan horses accounted for the largest share at that time.
Circulation
In 2008, security companies such as F-Secure expected "one million new malware programs". According to this, around 25,000 new malware programs - so-called unique samples, i.e. malware with a unique "fingerprint" according to MD5 - reach specially set-up servers, e.g. honeypots, every day. In contrast, AV-Test was able to count ten million new malware programs in 2008 as early as mid-April 2008. A strong change in the spreading of malware can be seen: Trojan horses in e-mail file attachments are becoming increasingly rare, while attacks via the web, for example by means of drive-by download, are on the increase. In addition, the use of rootkit techniques to hide the malware is becoming more common. According to the Californian malware specialist Kindsight Security, an average of 13% of private computers in Germany were infected by malware in 2012. According to a 2014 security study by <kes> magazine and Microsoft, "infection by malware" has moved up to first place among threats to corporate IT. It has thus displaced "employee error and negligence" to second place. Seventy-four percent of study participants said they had been affected by malware incidents in the last two years. In the companies surveyed, e-mail was at the top of the list of infection paths. This is followed by web content that distributes malware via active content or "drive-by downloads".
Motivation
In 2006, a study looking at the motivations of malware developers came to the five primary conclusions:
- Greed: Attacks are carried out in order to achieve a personal, material gain from them.
- Curiosity: Attacks are carried out to satisfy personal curiosity.
- Espionage: Attacks are carried out in order to obtain specific information.
- Retaliation: Attacks are carried out to cause targeted damage and to satisfy personal emotions.
- Conspiracy: Attacks are carried out to throw any pursuers off the scent.
A further component has now been added in the form of so-called cyber warfare, which goes far beyond simple espionage. A well-known example of sabotage by intelligence agencies was the network worm Stuxnet, which became known in 2010. This govware was used to manipulate Iranian nuclear facilities.
Questions and Answers
Q: What does malware stand for?
A: Malware stands for malicious software.
Q: What are the different types of malware?
A: The different types of malware are viruses, Trojan horses, spyware and ransomware.
Q: What can malware do to a computer?
A: Malware can steal passwords, delete files, collect personal information, or even stop a computer from working at all.
Q: How can computer security or anti-malware software help prevent malware from installing itself?
A: Computer security or anti-malware software can help prevent malware from installing itself by detecting and blocking it before it can do any harm.
Q: What happens when security software is not installed?
A: When security software is not installed, malware can easily get into the computer and cause damage.
Q: Is it easy to get rid of malware?
A: No, getting rid of malware can be difficult, even when using programs designed to remove it.
Q: Does unintended harm due to software bugs count as malware?
A: No, the term "malware" only refers to software that is intentionally designed to cause harm and works against users' expectations. Applications that may do unintended harm due to software bugs are not considered malware.
Search within the encyclopedia