Firewall (computing)
![]()
This article deals with firewalls within a computer network. For other meanings, see Firewall (disambiguation).
A firewall is a security system that protects a computer network or an individual computer from unwanted network access. More broadly, a firewall is also a partial aspect of a security concept.
Every firewall security system is based on a software component. The firewall software is used to restrict network access based on sender or destination and services used. It monitors the traffic passing through the firewall and decides whether or not to allow certain network packets through based on set rules. In this way, it attempts to prevent unauthorized network access.
Depending on where the firewall software is installed, a distinction is made between a personal firewall (also called a desktop firewall) and an external firewall (also called a network or hardware firewall). In contrast to the personal firewall, the software of an external firewall does not work on the system to be protected itself, but on a separate device that connects networks or network segments with each other and, thanks to the firewall software, simultaneously restricts access between the networks. In this case, "firewall" can also stand for the entire system (a device with the described function). Due to their design, there are major conceptual differences between the two types.
The function of a firewall is not to detect attacks. It should only implement rules for network communication. So-called IDS modules are responsible for detecting attacks. These modules can be based on a firewall and be part of the product. However, they are not part of the firewall module.

The personal firewall software runs on the computer system to be protected and restricts access to the computer's network services. Depending on the product, it can also attempt to prevent unauthorized access to the network by applications within certain limits, see below.
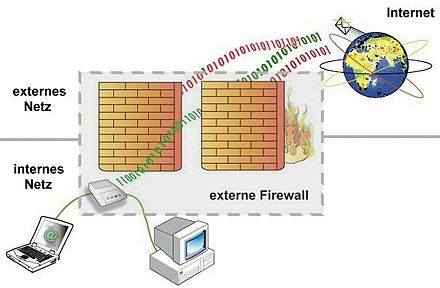
The external firewall is located between different computer networks. In this example, it restricts network access from the Internet (external network; WAN) to the private (self-contained) network (internal network; LAN). It does this, for example, by allowing through (response) packets requested from the internal network and blocking all other network packets.
General principles
The following basic knowledge is helpful for understanding how a firewall works. The respective main articles present the topics in detail.
How remote access to a computer system works
→ Main article: Network service and network protocol
Accessing a network service
A network service is a computer program that provides access to resources such as files and printers over a network. For example, Internet pages are stored as files on a computer (server). Only a network service running on the server (in this case, web server software) makes it possible to access the pages from the Internet and thus load and display them on a remote device. For network services to be accessible from the network, they each bind to a port on the network interface. They are said to "open a port", which conversely means that an open port always belongs to a computer program that can accept network requests.
A vulnerability in a network service can provide the basis to perform actions on the computer beyond the allowed access functions.
Note: A service (under Microsoft Windows English Service; under Unix English Daemon) is characterized by the fact that it is executed at every system start, regardless of whether a user logs on to the computer. There are programs with a functionality corresponding to the network service, i.e. they open a port but are only started after the user logs on. Although these programs are not strictly speaking services, they are also referred to as network services in the following for the sake of simplicity.
The return path from the remote network service to the client
The return path from the remote network service to the requesting PC (more precisely, the client), which accesses the service, can sometimes be used for overlapping remote access. To stay with the above example, the user starts a browser that is supposed to display web pages from the Internet on his PC. If the browser contains a corresponding security vulnerability, the contacted Internet server can now access this PC and perform actions there that go beyond the normal display of Internet pages. In the worst case, simply calling up a suitably prepared Internet page is enough to even secretly install malware on the PC. Malware can in turn operate as a network service on the PC and thus enable constant remote access to the PC.
Instead of installing a network service on the PC, the malware can also connect to the Internet on its own and connect to a network service that operates on the Internet. For example, a botnet usually runs this way. In such a case, the return path is used for constant remote access to the PC.
The network implementation of the operating system
For communication in the network, the computers involved - or the services installed on them ("communication partners") - require knowledge of the basic protocols used for addressing and transporting data. Sometimes an incorrectly implemented network connection of the operating system (including faulty driver software) can be used for network access that was not intended by the manufacturer in this form. An example of exploitation of a formerly widespread flaw in the implementation of the IP protocol is Ping of Death, which specifically crashed the target system. Similar gaps sometimes also allow program code to be infiltrated and executed on the target system.
Protective function and limits of a firewall
A firewall is used to prevent unwanted access to network services. It is based on the addresses of the communication partners (i.e. "who is allowed to access what"). As a rule, a firewall cannot prevent the exploitation of a security hole in the network service if the communication partner is allowed to access it.
When exploiting the return path, a firewall cannot protect against access to browser vulnerabilities if the communication partner can access the vulnerable areas of the program. Therefore, programs intended for network access should be kept up to date in order to close known security holes there. Some firewalls offer filters that further restrict remote access to the network service being used, for example by filtering vulnerable ActiveX objects from web pages. The browser can then no longer access such objects embedded in a web page (it does not display them), which at the same time means that it cannot be attacked via these objects. Alternatively, this behavior can also be achieved via the configuration of the browser used.
Depending on the firewall type, a firewall can, in the best case, draw attention to the network access of a secretly installed malware and sometimes even prevent its network access. However, such success is highly dependent on the skill of the respective malware (see the limits of the personal firewall and the external firewall).
At best, a firewall can prevent the exploitation of errors in the network implementation of the operating system.
The demonstrated limitations of a firewall compared to its benefits can be compared to the seat belt of an automobile, for which there are also scenarios in which it is not able to protect the driver. It makes sense to wear the seatbelt while driving carefully with the knowledge of its limitations. An exception could be a seatbelt that puts the driver at risk at the same time (here with reference to the personal firewall), which may mean that alternative solutions offer a higher level of safety.
The firewall as part of a security concept
Only when it is known against which scenarios a certain level of security is to be achieved, can one think about how this is to be implemented. The creation of a security concept helps here. In larger organizations, a separate security policy is usually used for this purpose.
The firewall is a partial aspect of the security concept. Just as "fire protection" is a bundle of measures (and not just the smoke detector in the stairwell), this partial aspect can be a bundle of several measures depending on the security concept. The firewall can consist of several components, some of which supply a DMZ, for example. Likewise, maintenance can be an integral part of the sub-aspect, as can the evaluation of logging of firewall components.
Filter technologies
→ For a detailed description see Firewall technologies
Packet filter
→ Main article: Packet filter
The simple filtering of data packets based on network addresses is the basic function of all firewalls (in a TCP/IP network this means more precisely the filtering of the port and the IP address of the source and target system).
stateful packet inspection
→ Main article: Stateful packet inspection
This stateful filtering is an extended form of packet filtering. This makes it possible to restrict access to an established connection more precisely and thus better protect the internal network from unwanted access from outside.
Proxyfilter
→ Main article: Proxy (computer network)
A proxy filter establishes the connection to the target system on behalf of the requesting client and forwards the response from the target system to the actual client. Since it conducts the communication itself, it can not only view it, but also influence it as desired. Specializing in a particular communication protocol, such as HTTP or FTP, it can thus analyze the data coherently, filter requests and make any adjustments as needed, but also decide whether and in what form to forward the target's response to the actual client. Sometimes it is used to cache certain responses so that they can be retrieved more quickly for recurring requests without having to request them again. Several such filters are often used in parallel on a single device in order to be able to serve different protocols.
Content filter
→ Main article: Content filter
This content filter is a form of proxy filter that evaluates the user data of a connection and is intended, for example, to filter out ActiveX and/or JavaScript from requested web pages or to block generally known malware when downloading. It also includes the blocking of undesired web pages based on keywords and the like.
deep packet inspection
→ Main article: Deep Packet Inspection
Deep packet inspection can be used to analyze further information, especially protocol-specific information. This makes it possible to use rules based on URLs, file names, file contents (virus scan or data loss prevention) and the like. This is similar to the possibilities of a proxy or a content filter, but usually covers numerous protocols.
In order to also be able to analyze encrypted connection data and content, SSL Deep Packet Inspection is used, which terminates an existing SSL encryption, examines the content and then re-encrypts it for the client. For this purpose, it is usually necessary to install a CA root certificate on the client, which allows the firewall to generate suitable certificates itself during operation. Technically, this corresponds to a man-in-the-middle attack.
Visibility for users
→ Main article: Network Address Translation
To be able to filter network packets, the firewall must be located between the communication partners. It can appear to the communication partners in different ways, whereby the first four appearances can only occur on an external firewall:
Visible
The firewall acts as an intermediary visible to both sides between the source and target systems. Here, the client asks the proxy firewall to take over communication with the target system on its behalf. For example, the web browser is configured so that it does not send all Internet requests directly to the respective target address, but sends them as a request to the proxy. The proxy then establishes the connection to the target system. Only after the analysis is complete does the proxy forward the response from the target system to the requesting client.
Transparent to one side
One of the two sides addresses the destination directly here and not the firewall. Due to an appropriately configured infrastructure of the network, the request in question is automatically routed through the (NAT or proxy) firewall there without the sender noticing or even being able to influence this. The connection to the other side is now established via the address of the firewall. Possible attacks from there are also directed at the firewall here and do not hit the client directly. This is because for this side the firewall represents the communication partner to be addressed, which is addressed as a proxy for the actual communication partner. This form is the most common type of firewall devices for the home.
Transparent to both sides
Here, the firewall is transparently (almost invisibly) placed between both networks and thus enables a continuous connection of the communication partners, so that the systems in front of and behind the firewall can see each other directly. The data stream simply flows through the firewall. At the level of IP addressing, the remote station therefore does not see the firewall as a communication partner, but only recognizes it as a connecting link between the subnets (router without NAT). Nevertheless, the firewall software running on the network device (router) can interrupt the data stream (filter out certain packets).
Invisible
Just as with the two-way transparent mode, the data stream here simply flows through the firewall. However, the device running the firewall software now works like a bridge, making it invisible to the communication partners neither at IP level nor from a low-level addressing perspective.
Local
Firewall software installed locally on the computer (personal firewall) monitors the data stream flowing through it locally (on the computer whose network packets it is supposed to filter; called source system in this paragraph). From the point of view of the target system, the firewall is therefore located behind the network adapter of the source system. This changes neither the network address of the source system nor the communication path to the target system. Thus, the personal firewall is also practically invisible from the addressing point of view. However, this only refers to the communication path and does not mean that it cannot be detected (due to the behavior of the source system) or that it cannot be directly attacked via the address of the source system (in contrast to the external bridge firewall, which has no network address).
Rulebook
→ Main article: Firewall rules
The rules of a firewall determine what should happen to a network packet that fits the pattern of a filter. The actions can be titled differently depending on the product. Either the request is not allowed and the packet is discarded locally (usually called DROP) or it is actively rejected (REJECT), for example by being answered with an ICMP packet. A permitted request is called ACCEPT, ALLOW, PASS or FORWARD, whereby FORWARD can also indicate a redirection of the request, depending on the product and configuration.
Verifiability of the source code
→ Main articles: Proprietary software, open source and free software
In the case of software products, free access to their source code is an aspect of computer security. Among other things, it is important to minimize the risk that a product may contain functionalities that the user is not supposed to know about. For example, there are some closed-source products in the area of personal firewalls that themselves secretly send data to the manufacturer, i.e. do exactly what some users are actually trying to prevent with the product. Open source software can be checked by the public in this respect and can also be examined for vulnerabilities by legally unobjectionable means, which can be closed more quickly in this way. Open source licensing models are not the same as free software; open source and free software also include commercial products (free software is not the same as freeware).
Firewall Technologies
A firewall can distinguish desired from undesired network traffic using various methods, but not every product supports all of them.
Packet Filter Firewall
→ Main article: Packet filter
The task of a packet filter firewall includes blocking or allowing through network packets based on their network address. To do this, it evaluates the header information of the network packets.
Simple (stateless) packet filtering works on a firewall router with static rules and considers each network packet individually. It therefore does not establish any relationships with the previous network packets. In contrast, there is an advanced form of (stateful) packet filtering that captures such relationships by relying on the technique of stateful inspection. This further restricts access to the source system that requested a communication. A corresponding firewall is also classified as a pure packet filter firewall, at least as long as no (possible) proxy filters are installed on it.
Network addressing as the basis for packet filtering
→ Main article: MAC address, IP address and port (protocol)
Each network card has a unique, retrievable serial number called a MAC address. It is composed of a manufacturer identification number and an adjacent serial number.
Since these numbers are unique, they can be used for a simple but generally valid type of addressing in a network. Simple because, for example, a computer can be addressed in an unbranched network, but the MAC address cannot specify the computer's program for which the network packet is intended. Unbranched because the MAC address, due to its structure, is not suitable for being broken down into further sub-areas. An assignment of the addressee to a specific subnet is therefore not possible with the MAC address. In other words, MAC addresses can be used like house numbers, but cannot be assigned to a street or an inhabitant of the house.
The solution is provided by higher communication protocols that are placed over the MAC address. A network packet is therefore figuratively packaged several times, with the MAC address representing the outer packet and the other packets being inserted layer by layer in this packet. Within a TCP/IP network, the IP address forms the next higher protocol, i.e. the next packaging. It is several blocks of digits, comparable to a house address containing a street number and a house number (which part of the IP address symbolically represents the street number, more precisely the network ID, and which part represents the house number, more precisely the computer ID, is defined by the subnet mask). In such a network, the next higher protocol, i.e. the packaging after the IP address, represents the port. The port is comparable to a room number or a name tag. It determines for whom exactly "in the house" the packet is intended (more precisely: which program should receive the packet).
A firewall can evaluate all of this "packaging" and filter the network packets accordingly by deciding which requests are allowed and which are not based on a "who is allowed to access what" set of rules. However, this is usually only done from OSI layer 3, i.e. the IP address, since the MAC address information of the network packets changes when they pass through a router on their way through the network, for example.
Address filtering is the basic form of all other types of firewall. Filters that serve purely to filter network addresses, i.e. packet filters, are therefore also found on all other firewalls.
Firewall Router
A firewall router is classified as a packet filter firewall and is software installed on a router where it restricts the network connection. This type of firewall can appear in one-way transparent mode (router in NAT mode) or two-way transparent mode (router without NAT).
It is mainly associated with firewall devices that use static (stateless) packet filters, although strictly speaking a stateful inspection firewall can also be based on a router. Other types of firewall thus differ from a firewall router in that they at least offer a more precise form of packet filtering (stateful inspection) or are based on a different concept from the router, usually offering an extended form of filtering in addition to the packet filter (such as proxy firewall and personal firewall).
The firewall router is very fast compared to other types of firewalls with the same hardware.
OSI layers
→ Main article: OSI model
The OSI layer model describes the design basis of communication protocols in computer networks. According to this layer model, a packet filter accesses OSI layer 3 (IP address) and 4 (port) from the header information of a network packet.
Example of a set of rules
→ Main article: Firewall rules
In the following exemplary filter rules, it should be noted that the filtering is not based on the content of the named protocols, but on the TCP or UDP ports belonging to the corresponding network service:
- Mail services (SMTP - TCP port 25, POP3 - TCP port 110 and IMAP - TCP port 143) are allowed from the Internet to the mail server in the DMZ.
- The mail server is allowed to send mails from the DMZ to the Internet via SMTP and to make DNS requests.
- Administration services (SSH, Remote Desktop, Backup - TCP port 22) to the mail server are allowed from the local network.
- All other packets in or out of the DMZ are written to a log file and then discarded.
The filtering decisions are made individually and independently for each packet. This type of filtering is implemented in many routers and Layer 3 switches today.
stateful inspection
→ Main article: Stateful packet inspection
In contrast to the static (stateless) packet filter, the firewall rule is specified dynamically for each connection request in order to restrict access to an established connection more precisely. In doing so, the firewall directly relates the return channel (destination to source system) to the previously established connection (source to destination system) and restricts access accordingly so that only the involved communication partners can access the connection. This is the basic function that all stateful inspection firewalls are capable of.
Special filters of numerous stateful inspection firewalls can also view the user data of a communication. This is useful, for example, for network protocols that use the user data to negotiate a second connection between the communication partners (see active FTP). The insight into the payload data allows the filter to further specify the address filtering of the packets, but unlike a proxy filter, it is not able to influence the connection itself (it cannot change the data).
Depending on the product, the stateful inspection firewall can also detect after a connection has been established whether and when the PC to be protected (more precisely, the client) communicates with the target system, with the firewall only allowing responses if this is the case. If the target system sends data that was not requested by the client, the firewall blocks the transfer even after the connection between client and target system has been established.
OSI layers
→ Main article: OSI model
A packet filter based on the stateful inspection technique accesses OSI layer 3 (IP address), 4 (port) and possibly 7 (user data) of a network packet.
Possible functions
Depending on the configuration of the device on which the firewall software is installed and the firewall product, a stateful inspection firewall can provide the following features, among others:
- Protection against SYN flooding, e.g. through SYN cookies
- Discarding of faulty packets (e.g. conflicting TCP flags like SYN bits, ACK bits and sequence numbers)
- Protection against Ping of Death, Smurf attacks, Teardrop attacks or Land attacks
Proxy Firewall (also Application Layer Firewall)
→ Main article: Proxy (computer network)
In addition to the pure traffic data such as source, destination and service, the filters of a proxy firewall (also known as an application layer firewall) typically also consider the user data, i.e. the content of the network packets. In contrast to stateful inspection technology, which sometimes also accesses the user data depending on the product, the typical proxy filter does not simply pass on the network request of the source system to the target system. Rather, it establishes its own connection to the target system. Since it communicates with the target system on behalf of the requesting client, it can analyze the packets coherently and influence the connection. It is thus able to filter requests with regard to the communication flow of the user data and can decide which responses from the target system it passes on to the requesting client. In doing so, it can change the packet content as desired.
Technically, such a filter works as a communication partner intervening in the traffic, terminating the connections on both sides (they are two independent connections) instead of passing the network packets. The filter itself is a computer network utility that mediates in traffic, and is therefore also called a proxy server: As an active mediator, it behaves like a server to the requesting client and like a client to the other side, the destination system. Since it must know the communication protocol, it has its own filter for each higher communication protocol (HTTP, FTP, DNS, SMTP, POP3, MS-RPC, etc.) (this is why they are also called dedicated proxies). Among other things, they can prohibit unwanted protocol options, for example by not allowing BDAT, VRFY, etc. in an SMTP transaction. There can even be several dedicated proxies for one and the same protocol, for example, to filter different web services under HTTP; for example, one for each web application used in a company.
The generic proxy, also called circuit level proxy, is an exception. It is used as a protocol-independent filter on the proxy firewall, where it implements a port- and address-based filter module that also supports (possible) authentication for establishing the connection. The filter is not able to view the communication, to conduct it itself and to influence it, since it does not know the communication protocol.
See also: Web Application Firewall
OSI layers
→ Main article: OSI model
A dedicated proxy as a filter that specializes in a specific protocol works as an intermediary utility and therefore accesses OSI layer 7 (application layer) (like any utility or application program). The circuit level proxy as a generic (protocol-independent) filter, on the other hand, uses OSI layer 3 (IP address), 4 (port) and, if necessary, 5 (for authentication for establishing the connection).
Note: Contrary to popular misunderstanding, the basic task of an application layer firewall is not to grant or deny certain applications (programs) access to the network. The name Application was merely derived from the application layer of OSI layer 7, which stands for the fact that a corresponding filter can look into the user data of the network packets. The task of restricting network access to applications that have authenticated themselves to the firewall usually falls (if at all) to the generic proxy filter, i.e. the filter that does not even use the application layer.
Borders: Tunneling Through
→ Main article: Tunnel (computer network)
In principle, any service can work on any port number. If TCP port 80 is enabled for HTTP in the set of rules, another protocol can still run over it. Only both communication partners (the client in the internal network as well as the service on the server from the external network) must be configured accordingly. An attempt to prevent this using the firewall can be made with application layer firewalls. They can examine the structure of the user data and block all packets that do not correspond to the protocol of the released service. However, each protocol is supposed to transmit data, so in this case the data just needs to be converted accordingly. If the software embeds the data to be transmitted in HTTP without violating the standard of the protocol, this firewall is also powerless against it (the remote station, the service on the server, must understand this type of conversion, however). A tunnel performs such a conversion. Manipulated data can, for example, be data streams packaged in image data.
Tunnels therefore provide a method to bypass the control of a firewall. Tunnels are also used to transport insecure network protocols using a secured and encrypted network protocol to prevent eavesdropping and tampering. This can be done, for example, through an SSH or VPN tunnel within a legitimately enabled connection.
Both OpenVPN and many SSH clients (e.g. PuTTY) are also able to establish a tunnel via an HTTP proxy, which should actually only forward websites. In addition, there is special tunnel software for protocols such as DNS or ICMP.
Skype in particular is an example of how well most firewalls can be bypassed from the inside out. As long as users from the internal network are able to access websites, the firewall administrator has technically little chance to prevent tunneling through due to the encryption. Thanks to whitelists that restrict access to certain servers, firewalls can at least make tunneling through much more difficult. Organizations sometimes augment the technical measures with organizational security measures, such as a ban on deliberate tunneling in the security policy that the employee must sign.
Transparent piercing of a firewall is also called firewall piercing.
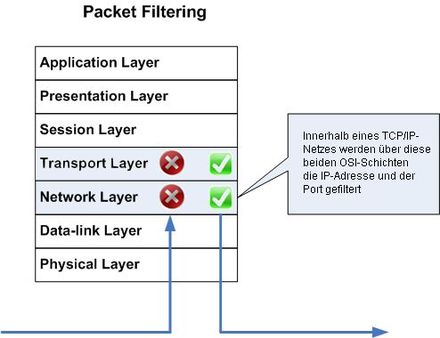
OSI layers: Packet filter of a firewall
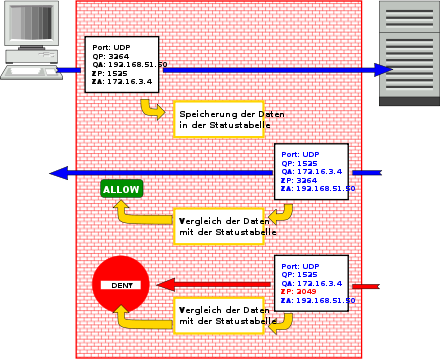
Stateful inspection: The properties of outgoing data packets are stored in a status table. Incoming data packets are compared with this table.
Questions and Answers
Q: What is a firewall?
A: A firewall is a piece of software used in computer security that monitors network traffic between trusted and less trusted networks and applies a set of rules to each packet.
Q: What does a firewall do?
A: A firewall protects a part of the network against unauthorized access by applying a set of rules to each packet of network traffic passing through it.
Q: What networks does a firewall protect?
A: A firewall is placed between the network that is to be protected (trusted) and the outside network (less trusted) such as WAN or Internet.
Q: Where is the firewall placed in a network?
A: The firewall is placed between the trusted network and the outside network (less trusted) such as WAN or Internet.
Q: What are the rules applied by a firewall?
A: A firewall's set of rules determine whether a packet of network traffic can pass through to the trusted network or whether it is discarded.
Q: How does a firewall function?
A: The firewall monitors network traffic passing between the trusted and less trusted networks and applies a set of rules to each packet to decide whether it can pass through or not.
Q: Does a firewall protect the entire network?
A: No, a firewall only protects one part of the network against unauthorized access.
Search within the encyclopedia